A federal appeals court ruled this week that Congress never granted the Federal Communications Commission authority to impose “network management” regulations on Internet service providers and that the FCC’s overly “expansive view” of its power did not merely strain the outer limits of its authority but “seeks to shatter them entirely.” In real terms, this rebukes the commission for its effort to order high-speed Internet service providers such as Comcast to treat equally all traffic that flows through their pipelines.
Despite this defeat, the FCC might still try to regulate the Internet under century-old rules made for railroads and Ma Bell phone monopolies. This mistaken effort would hinder recent successes in deploying broadband throughout the country.
While the U.S. economy has shrunk substantially over the past two years, the Internet sector has flourished. Increasingly, our commerce and culture ride on the rails of high-speed, or “broadband,” Internet access. But this success was not inevitable.
The Clinton administration set today’s “hands-off” policy when the Internet was privatized in the mid-1990s. Amid the rubble of the dot-com bust, in 2002 the FCC sought to energize the nascent broadband sector by formally insulating the Internet from regulation. The commission classified broadband as unregulated “information services,” establishing a framework that was designed to attract the investment of risk capital, foster competition, lower prices, fuel innovation and increase consumer adoption.
It worked. In 2003, about 15 percent of American adults had access to broadband at home, according to a Pew Internet & American Life Study. Today that number is closer to two-thirds. Some form of broadband is available to roughly 95 percent of Americans.
Mobile broadband was virtually unheard of in 2002. By the end of last year, an estimated 100 million Americans subscribed to wireless broadband services. We lead the world in 3G networks.
Not only have investment and innovation been dynamic in core telecom areas, but cutting-edge economic activity has exploded. Last year Americans led the world by downloading more than 1.1 billion applications onto their mobile devices. (We should stop calling them phones; they have become our mobile computers.) That’s a ninefold increase from just two years earlier. An entire industry for mobile apps has solidly taken root.
The Web’s free and open marketplace is thriving — and evolving faster than any government or company can measure. It is, in short, the greatest deregulatory success story of all time.
Yet some seek government regulation of this constructively chaotic part of our economy.
Last fall, over dissenting votes from Commissioner Meredith Attwell Baker and me, the FCC proposed rules to regulate high-speed Internet. Before embarking on any regulatory journey, it is critical for the government to ask and answer: What exactly is broken that only the government can fix?
Curiously, the commission proposed rules even though studies by the FCC and the Federal Trade Commission found no evidence of market failure. And when the Justice and Commerce departments filed comments with the FCC in January, neither provided evidence of concentrations and abuses of market power in the broadband arena. To the contrary, the Justice Department sounded optimistic about the competitiveness of the broadband market. It even warned against imposing new regulations “to avoid stifling the infrastructure investments needed to expand broadband access.”
Nonetheless, the FCC may still consider imposing early-20th-century vintage “common carrier” regulations on 21st-century broadband technologies. One result of the new rules could be to make it harder for the operators of broadband “pipes” to build “smart” networks, which offer connectivity and other services or products.
As the distinction between network operators and application developers blurs, how will government keep up? Internet application developers own massive server farms and fiber-optic connectivity. Meanwhile, broadband companies develop and maintain software with millions of lines of code and have created app stores that are seamlessly connected to their networks. As technology advances, in the absence of market failure, should the government attempt to make distinctions between applications and networks under a new regulatory regime? Would it be able to do so in Internet time? Would any of this be good for innovation, investment and America’s global competitiveness?
And how will FCC actions be perceived internationally? Countries that regulate the Internet more tend to be less free than those that are hands-off. Not only are some countries waiting for Washington to assert more authority over the Internet to justify their own state interference with the Web, but once government regulation of the Internet starts, it will become harder to pull back.
We should also ask whether we want business decisions affecting the Internet to be caught up in election cycles. It is inevitable that more government involvement will mean enforcement decisions are politically influenced.
Policymakers ought to agree on a sensible middle ground. In lieu of new rules, which would be tied up in court for years anyway, the FCC could forge a partnership with the long-standing nongovernmental bodies that have collaborated on Internet governance for years. Working together, we could spotlight allegations of anticompetitive conduct and seek resolution. This approach, coupled with strict enforcement of our antitrust laws, could provide the benefits some are seeking without incurring the risks and costs of a regulatory regime.
The best antidote to potential anticompetitive conduct is more competition. Let’s work on policies that encourage more investment, innovation and competition instead of regulation and rationing.
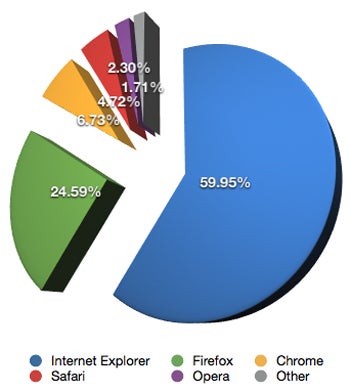 NetApplications browser market share statistics for April 2010.
NetApplications browser market share statistics for April 2010.